Q&A with GreatHorn - cloud security platform
 In this post we are talking to Kevin O'Brien, co-founder and CEO of GreatHorn , Techstars '15 company from Boston.
In this post we are talking to Kevin O'Brien, co-founder and CEO of GreatHorn , Techstars '15 company from Boston.
1. What is GreatHorn in 140 characters?
GreatHorn is a new kind of cloud security platform makes email safer by preventing spear phishing and credential theft attacks in realtime.
2. Why did you start the company?
I have been working in the cybersecurity space since the late 1990s; my co-founders have equally long backgrounds in the industry. We looked at the state of security late last year, and saw that over 90% of all successful cyberattacks started from the same basic kind of attack: a hyper-targeted email that tricked someone into clicking on a link or authorizing a financial transaction to an attacker.We were astounded that the market solutions relied on either outdated on-premise hardware that companies had to install in a server room -- not very useful if you're using a modern system like Office 365 or Google Apps to run your email! -- or training courses and hope.Security shouldn't work this way; it should be ambient, automatic, and easy to deploy. We built GreatHorn on this belief.
3. What does your product do?
GreatHorn is a new kind of security platform that prevents email based attacks by automatically helping recipients understand whether an email they just received is safe.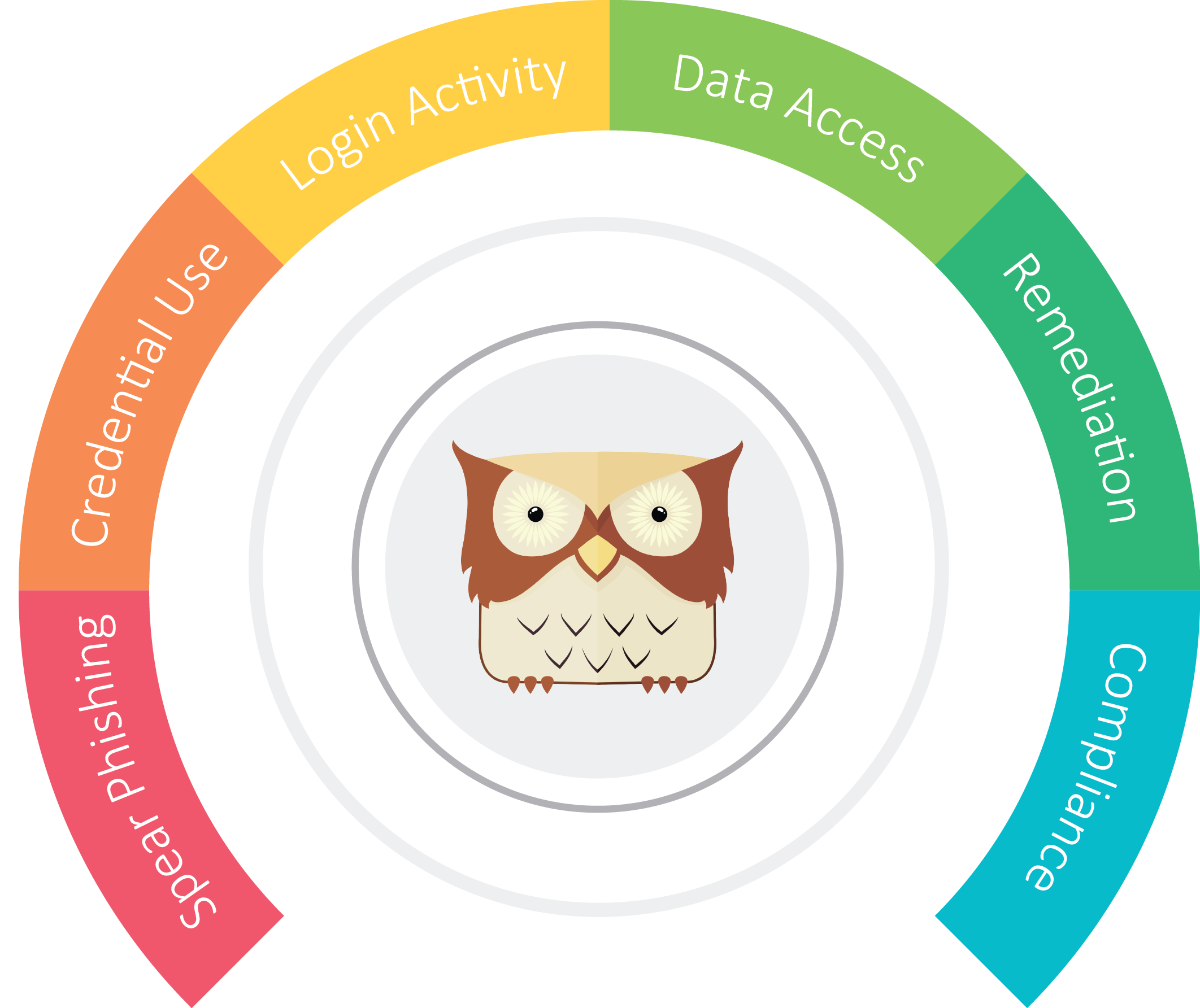 We plug directly into today's major email providers like Google Apps and Office 365, and in realtime, we analyze every message for both externally observable indicators of threat as well as indicators that only we can see, based on the huge amounts of messaging data we analyze on a daily basis.
We plug directly into today's major email providers like Google Apps and Office 365, and in realtime, we analyze every message for both externally observable indicators of threat as well as indicators that only we can see, based on the huge amounts of messaging data we analyze on a daily basis.
4. What are top things people need to pay attention do avoid being spear phished?
Take the problem seriously. Automate your defenses. Don't wait for a major financial loss to protect yourself.Earlier this year, we saw a major telecommunications company lose nearly $50m when their Chief Accounting Officer was spear phished. He thought he was sending out wire transfers on the orders of his CEO -- only to find out that the emails were sophisticated fakes, and he nearly bankrupted the business.Understanding that smart attackers are working tirelessly to deceive your staff means automating the work that goes into analyzing messages for these kinds of tricks. Training and manual forensics are great, but you need some way to look at every message header, every sender-to-recipient relationship, and catch every attempt at a wire transfer, all before they lead to a breach.
5. Who are your customers?
We protect over 6,000 mailboxes today, from HMOs to technology companies to financial transaction providers. Organizations with regulatory requirements (like healthcare and financial services) have seen particular value in the kind of protection we've created, and we're actively engaging organizations from the micro to the multinational as we move into FY16.
6. What are your key KPIs and how did you choose them?
Revenue and pipeline are what I look at on a daily basis.While my security background is technical, I've been mentored by amazingly good sales people and sales management over the years. As a founders at a previous company I was part of once pointed out to me, growth defines startups, and good sales fundamentals are essential in getting there.We also keep a close eye on our tech, and track both the number of mailboxes we protect as well as the number of emails we analyze and defend. We pull in more than a million new messages every week, from multiple companies, and that growth curve gives us an unique opportunity to find threats faster and more accurately than anyone else in the market today.
7. What is your long-term vision for the company?
We think cloud-based communication is changing how businesses interact with the world. Constant accessibility is the new normal. It's easier than ever to reach any person in the world, on a huge range of systems and at any time of day -- but in conjunction with this increase in convenience comes a decrease in the ability to be certain that the person you are interacting with is who they say they are.This kind of dispersed infrastructure requires a fundamentally different approach to trust and security, one that operates without getting in the way of doing business and is highly visible to the end user.We're building that system, based on the belief that services such as Google Apps and Office 365 will become the central hub around which all business communication will orbit. Defend those services without becoming an impediment to business communication, and you can provide a practical solution for also protecting everything from Slack to Skype to Yammer, no matter where they are accessed from.Our vision is to be the cloud communication security provider, protecting every organization from threats that attempt to exploit the trust everyday users of those systems.
8. What is your advice to your fellow founders?
Aside from "get into Techstars?" :)Build a real financial model. We exist in a moment when everything about starting a business is easier than it was a decade ago: you don't need the same capital to stand up hardware that you once did, and there are more ways to capitalize your business than I can ever recall. As a result, it's sometimes easy to get seduced by the artifacts of company building: hiring big teams, renting fancy offices, spending a lot of time talking to investors and to the press.Dollars raised are a tool. Dollars returned are the business. The hard work of acquiring, delighting, and building out an ultimately profitable customer base is where your true north should be -- everything else, even investment, is a means to that end.Less philosophically: know your numbers. Stress test them often. Be humble along the way.